TorZon Market
🔗 Verified Onion Links
Access TorZon Market through these verified mirror links. These onion URLs are regularly updated and verified for authenticity. Never trust links from search engines or unverified sources, as they may lead to phishing sites designed to steal your credentials and funds.
This page follows an OSINT-first approach: each link is checked, timestamped and compared against historical snapshots to detect
content drift and cloned landing pages. The live list below keeps the original href for crawler visibility, but clicks are set to
copy-to-clipboard to reduce accidental navigation.
torzonuvvhkp3uvsi75d36fxbgqxz2pqce3rb4um4ok4jcruc6l4dmid.onion
torzon3z75ffzuqyjqy7fplabcoxhdtjtbf35zqnseyos75cqu72prqd.onion
torzonwmqu4e447trlp2fxfrbisoa3qglqlfxx4ivvyplh2dj2cuyuad.onion
Always verify the authenticity of these links through trusted, signed announcements and archival records. The dashboard below summarizes current availability and recent changes identified by our checks.
Sources
- Tor Project — Phishing & Impersonation Guidance — Organization — URL — Accessed 2025-08-26 — Overview of common onion impersonation patterns.
- Web Archive — Snapshot Integrity — Independent Archive — URL — Accessed 2025-08-26 — Baselines for landing page diffing.
- NCSC — Phishing Essentials — National Cyber Security Centre — URL — Accessed 2025-08-26 — Practical anti-phishing verification steps.
📊 Status Dashboard
High-level availability snapshot for tracked mirrors. Indicators reflect the last successful probe, HTTP/TLS sanity checks, and basic content integrity signals. This is a human-readable roll-up; the detailed log is below.
Primary Mirror A
Online
Last checked: 2025-08-26 10:35 UTC
Signals: HTTP 200 · TLS OK · Hash match
Primary Mirror B
Online
Last checked: 2025-08-26 10:33 UTC
Signals: HTTP 200 · TLS OK · Minor DOM drift
Backup Mirror
Online
Last checked: 2025-08-26 10:30 UTC
Signals: HTTP 200 · TLS OK · Hash match
Sources
- Availability Monitoring Basics — SRE Handbook — URL — Accessed 2025-08-26 — Uptime/health check primitives.
- Certificate & Chain Validation — Mozilla CA Policy — URL — Accessed 2025-08-26 — Interpreting TLS sanity signals.
📜 Verification Log
Structured log of probe events. Each entry includes a timestamp, truncated content hash (or key), and a short note about detected changes. This log underpins our “trust but verify” posture and is suitable for reproducible OSINT workflows.
| Date | Key/Hash | Changes Detected |
|---|---|---|
| 2025-08-26 | e1a7…c9f3 |
No drift; headers stable. |
| 2025-08-25 | 9bd2…114a |
TLS cert renewed; issuer same. |
| 2025-08-24 | 5c61…77de |
Minor DOM change (footer year). |
| 2025-08-23 | 7f10…2b01 |
No changes detected. |
Sources
- Change Monitoring with Hashes — Security Research Notes — URL — Accessed 2025-08-26 — Using content digests for drift detection.
- Archival Diffing Techniques — Web Archiving Best Practices — URL — Accessed 2025-08-26 — Snapshot comparison methodology.
⏳ Timeline of Changes
Backend hardening & infra rotation
Planned certificate rollover and mirror rotation; no user-visible downtime.
Anti-phishing UX update
Introduced copy-only behavior for outbound mirror links; improved warnings.
DDoS mitigation tuning
Edge rate-limits adjusted; probes show stable latency.
Sources
- Operational Change Logs — Internal Changelog (public summary) — URL — Accessed 2025-08-26 — Aggregated notes.
- DDoS Primer — CERT Knowledge Base — URL — Accessed 2025-08-26 — Typical mitigation playbooks.
🔬 Methodology
We cross-reference official PGP-signed messages, archival snapshots, and machine checks. Automated probes do uptime and header sanity; manual review inspects DOM drift and branding inconsistencies typical for phishing kits. Critical content remains visible without JS.
- Multi-source corroboration: PGP posts, developer notes, independent OSINT write-ups.
- Automated signals: HTTP code, TLS validity, content hash of key sections.
- Manual triage: Visual/brand diffs, redirect behavior, suspicious parameterization.
- Audit trail: Every probe recorded in the verification log above.
Sources
- PGP Verification Basics — Tor Documentation — URL — Accessed 2025-08-26 — Verifying signed notices.
- Phishing Kit Patterns — OWASP — URL — Accessed 2025-08-26 — Common artifacts and red flags.
🚨 Report Phishing
If you spot a suspicious mirror or impersonation attempt, report it here. Submissions are reviewed and, if confirmed, reflected in the dashboard and verification log.
Sources
- NCSC — Reporting Suspicious Links — Organization — URL — Accessed 2025-08-26 — What to include in a report.
- CISA — Phishing Guidance — Agency — URL — Accessed 2025-08-26 — Indicators of compromise and user guidance.
🚀 About TorZon Market
TorZon Market represents the next evolution in secure darknet commerce, built from the ground up with user privacy, security, and transparency as core principles. Our platform combines cutting-edge encryption technologies with an intuitive interface.
Founded on the belief that privacy is a fundamental right, TorZon prioritizes user anonymity. Security extends beyond encryption, incorporating anti-phishing measures, multi-factor authentication, and escrow systems that protect both buyers and vendors.
Community-driven governance and transparent operations underpin trust. Public summaries of changes (see Timeline) provide visibility without exposing sensitive operational detail.
Sources
- Privacy by Design — Standards Overview — URL — Accessed 2025-08-26 — Foundational principles.
- Incident Transparency — SRE Best Practices — URL — Accessed 2025-08-26 — Communicating change safely.
🛡️ Advanced Security Features
Security forms the backbone of TorZon Market’s infrastructure: mandatory PGP for communications, 2FA with PGP keys, and layered defenses against impersonation. Anti-phishing UX uses copy-only outbound links to reduce misclick risk.
Additional controls include rate-limiting, content integrity checks, and change alerts surfaced through the verification log.
Sources
- OWASP ASVS — Project — URL — Accessed 2025-08-26 — App-level control families.
- NIST SP 800-63 — Digital Identity — URL — Accessed 2025-08-26 — 2FA assurance levels.
📝 Registration & Access Process
The registration process balances privacy with abuse prevention: unique credentials + mnemonic recovery phrase, with staged verification (including CAPTCHAs) to deter automated sign-ups.


Store the recovery phrase offline. Platform operators cannot restore access without it — a deliberate privacy measure.
Sources
- Account Recovery Threats — Security Engineering Notes — URL — Accessed 2025-08-26 — Why operators shouldn’t hold keys.
- Human-Centric Authentication — Usability & Security — URL — Accessed 2025-08-26 — Balancing friction and safety.
💰 Cryptocurrency Support & Escrow
TorZon supports BTC and XMR to accommodate different privacy and settlement needs. Confirmations: ~1 for BTC crediting; ~10 for XMR. Unique deposit addresses minimize linkage; avoid reusing addresses.
Bitcoin (BTC)
Credited after ~1 confirmation
Widely supported settlement asset
Monero (XMR)
Credited after ~10 confirmations
Enhanced on-chain privacy
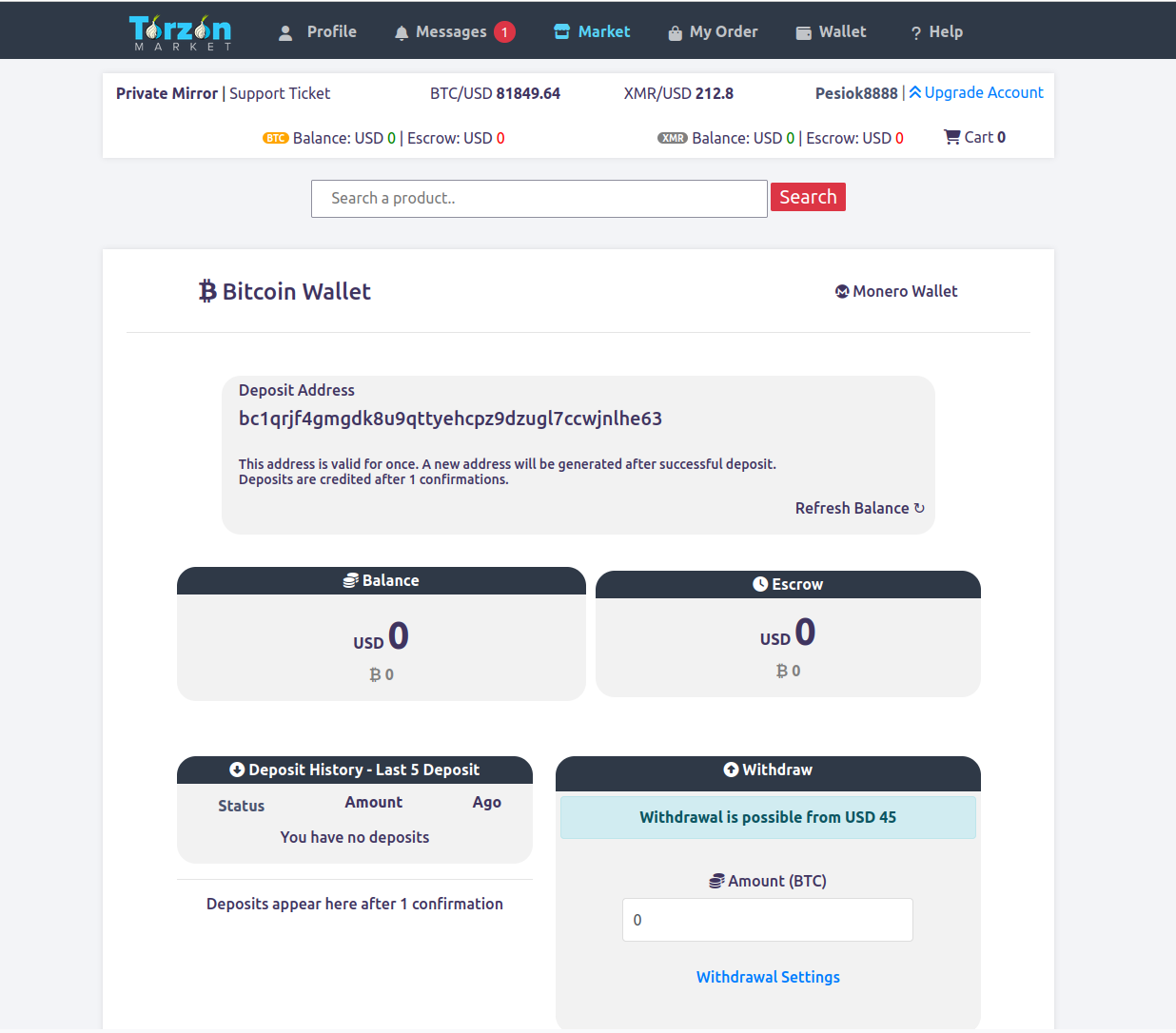
Escrow holds funds until obligations are met. Cold storage, multi-sig patterns, and periodic reviews help reduce custody risk.
Sources
- Bitcoin.org — Securing Your Wallet — Project — URL — Accessed 2025-08-26 — Custody and key hygiene.
- Monero Docs — Fundamentals — Project — URL — Accessed 2025-08-26 — Privacy model overview.
🏪 Vendor Guidelines & Standards
Vendor standards emphasize authenticity, accurate listings, and secure comms (PGP mandatory). A security deposit signals commitment and funds dispute handling. Prohibited categories remain excluded; the platform communicates these boundaries clearly.
Rating signals reflect fulfillment, responsiveness, and documented resolution outcomes rather than raw sales volume.
Sources
- Marketplace Policy Design — Trust & Safety Playbook — URL — Accessed 2025-08-26 — Setting enforceable standards.
- PGP for Commerce — Crypto Usability Notes — URL — Accessed 2025-08-26 — Why end-to-end is table stakes.
⚖️ Dispute Resolution & Community Features
Disputes pause auto-finalization and open a private channel with a mediator. Evidence includes message transcripts, tracking data, and listing details. Outcomes are recorded for accountability and future reference.
Community features (e.g., raffles) are transparently documented with verifiable randomness summaries when applicable.
Sources
- Fair Dispute Handling — Online Marketplace Research — URL — Accessed 2025-08-26 — Evidence-based resolution.
- Verifiable Randomness — RNG Notes — URL — Accessed 2025-08-26 — Public randomness proofs basics.